MCP Server-Sent Events (SSE) Explained
When building applications that integrate with AI models through the Model Context Protocol (MCP), you need effective ways for clients and servers to communicate. MCP offers two primary transport mechanisms: Standard Input/Output (STDIO) and Server-Sent Events (SSE). While STDIO works well for local process communication, SSE shines in web-based environments. Let's explore SSE and understand how it works in the MCP ecosystem.
What are Server-Sent Events?
Server-Sent Events (SSE) establish a unidirectional communication channel from server to client over HTTP. Unlike WebSockets which offer bidirectional communication, SSE creates a persistent connection where servers push updates to clients while clients use separate HTTP requests to send messages back.
The standard web format for SSE messages looks like:
data: Message content here
id: message-123
event: update-type
Each message can include data, an optional ID for tracking, and an event type for categorization. Browsers natively support SSE through the EventSource API, making it widely compatible across web platforms.
SSE in the MCP Architecture
The Model Context Protocol uses JSON-RPC 2.0 as its message format regardless of the transport mechanism. When implementing SSE transport, MCP wraps these JSON-RPC messages inside the SSE protocol.
The SSE transport in MCP combines:
- A persistent SSE connection for server-to-client messages
- Regular HTTP POST requests for client-to-server communication
The transport layer handles all the complexity of converting between MCP protocol messages and JSON-RPC format, making it transparent to the application logic.
How MCP Implements SSE
MCP's SSE implementation relies on a dual-endpoint architecture to enable full communication between clients and servers. First, the SSE endpoint serves as the primary channel where clients establish a persistent connection to receive streaming messages from the server. Meanwhile, the message endpoint functions as the complementary channel where clients send HTTP POST requests to communicate their needs back to the server.
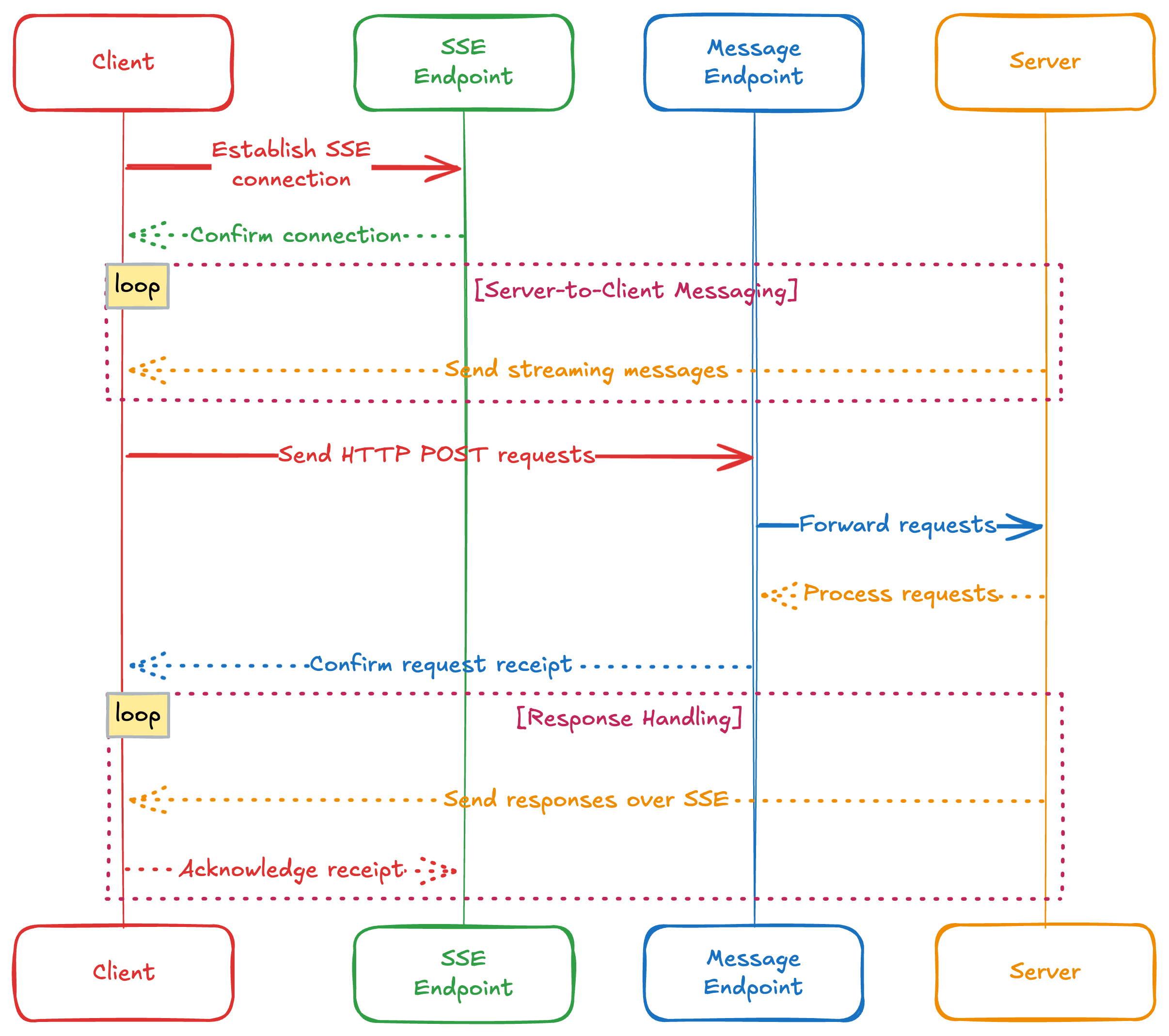 MCP Server-Sent Events Connection Workflow
MCP Server-Sent Events Connection Workflow
The communication flow begins when a client establishes an SSE connection to the server, creating the foundation for ongoing server-to-client messaging. After establishing this connection, the client can then send requests via HTTP POST to the message endpoint whenever it needs to communicate with the server. Once the server receives these requests, it processes them accordingly and sends responses back over the already established SSE connection. Finally, the client receives and processes these responses, completing the communication cycle.
Additionally, the server isn't limited to simply responding to client requests. It can proactively initiate its own requests or send notifications over the SSE connection at any time, without waiting for a client to make a POST request first. This asynchronous capability makes SSE particularly valuable for real-time updates and event-driven architectures where servers need to push information to clients as soon as it becomes available.
SSE vs STDIO: Choosing the Right Transport
Both SSE and STDIO serve as transport mechanisms in MCP, but they shine in different scenarios. Understanding their distinct characteristics helps you choose the right option for your application.
| Feature | SSE | STDIO |
|---|---|---|
| Communication Type | Network-based (HTTP) | Process-based |
| Web Integration | Native support in browsers | Not applicable |
| Security Concerns | Requires explicit security measures | Inherently isolated |
| Cross-platform | Works across network boundaries | Limited to local processes |
| Setup Complexity | Requires HTTP server configuration | Minimal setup |
| Performance | Network overhead | Direct, low-latency |
| Resource Usage | Higher (maintains HTTP connections) | Lower |
| Scaling | Supports multiple concurrent clients | One client per process |
When to use SSE:
- Web applications requiring AI integration
- Cross-domain or cross-network deployments
- Scenarios requiring server push capabilities
- When working with fire-walled environments that allow HTTP
When to use STDIO:
- Local desktop applications with embedded AI
- Command-line tools and utilities
- High-performance requirements with minimal overhead
- Security-sensitive applications requiring process isolation
- Single-client scenarios
The right choice depends on your specific application needs, deployment environment, and security requirements.
Basic SSE Transport Implementation
Let's look at a simple implementation of an SSE transport in TypeScript for both server and client sides:
Server-side implementation:
import express from "express";
const app = express();
const server = new Server({
name: "example-server",
version: "1.0.0"
}, {
capabilities: {}
});
let transport: SSEServerTransport | null = null;
app.get("/sse", (req, res) => {
transport = new SSEServerTransport("/messages", res);
server.connect(transport);
});
app.post("/messages", (req, res) => {
if (transport) {
transport.handlePostMessage(req, res);
}
});
app.listen(3000);
The server code sets up an Express web server with two critical endpoints. The /sse endpoint establishes the persistent Server-Sent Events connection when a client connects. It creates a new SSEServerTransport object that uses the provided response object to maintain an open connection for streaming data to the client.
The /messages endpoint handles incoming HTTP POST requests from clients, converting them into MCP protocol messages through the handlePostMessage method.
Client-side implementation:
const client = new Client({
name: "example-client",
version: "1.0.0"
}, {
capabilities: {}
});
const transport = new SSEClientTransport(
new URL("http://localhost:3000/sse")
);
await client.connect(transport);
On the client side, the code creates an MCP client and configures an SSEClientTransport that points to the server's /sse endpoint. When client.connect(transport) is called, it establishes the SSE connection and sets up the necessary event handlers. The transport automatically handles sending client requests to the server's /messages endpoint via HTTP POST while receiving server responses through the established SSE stream.
This asymmetric communication pattern — SSE for server-to-client and HTTP POST for client-to-server — forms the foundation of MCP's SSE transport mechanism.
Security Considerations
SSE transport introduces several security challenges you'll need to address as a developer:
1. DNS Rebinding Attacks
DNS rebinding attacks pose a significant threat, as they allow malicious websites to access local services by changing DNS records. An attacker could potentially trick a user's browser into connecting to local MCP servers running SSE. To protect against this vulnerability, you should always validate the Origin header on incoming SSE connections, only accept connections from trusted origins, and implement proper CORS policies.
2. Network Interface Binding
Network interface binding requires careful attention as well. Local MCP servers using SSE should never bind to all network interfaces (0.0.0.0). Instead, always bind specifically to localhost (127.0.0.1):
// Secure binding to localhost only
app.listen(3000, "127.0.0.1");
3. Authentication and Authorization
For public-facing SSE servers, authentication becomes crucial to prevent unauthorized access. Implement token-based authentication for all connections, validate credentials before establishing SSE connections, and set up proper access control mechanisms for different operations.
Practical Considerations
When implementing SSE transport for MCP, several practical considerations deserve your attention:
1. Connection Management
Connection management stands out as a key concern, since SSE connections might disconnect unexpectedly due to network issues or timeouts. Your implementation should handle reconnection gracefully through reconnection logic with exponential backoff. You'll also want to track message IDs to prevent duplicate processing after reconnection and utilize the Last-Event-ID header to resume from where the connection left off.
To mitigate connection issues, implement a robust reconnection strategy that increases wait times between attempts to avoid overwhelming the server during outages. Store the last received event ID client-side and send it with reconnection requests via the Last-Event-ID header, allowing the server to resume the stream from the right position.
Regular heartbeat messages sent every 15-30 seconds help detect silent connection failures quickly, as browsers may not immediately report dropped connections. Configure appropriate timeouts on both client and server sides, with industry standard recommendations suggesting at least 90 seconds before closing inactive connections.
2. Message Ordering
Message ordering presents another challenge, as client-to-server messages use separate HTTP requests that might arrive out of order. Your server must account for this possibility by using sequence numbers or timestamps to track message order. In some cases, you may need to buffer and reorder messages, and your protocol design should exhibit resilience to message reordering.
To address message ordering issues, assign monotonically increasing sequence numbers to all outgoing messages on both client and server sides. Maintain a message buffer on the receiving end that temporarily holds out-of-order messages until their predecessors arrive. Implement a message processing pipeline that sorts and handles messages in the correct sequence, with configurable timeouts to prevent indefinitely waiting for missing messages.
For mission-critical applications, add an acknowledgment system where receivers confirm message receipt, allowing senders to retransmit lost messages. Time synchronization between client and server also helps validate message timestamps for proper ordering.
3. Session Management
For stateful applications, session management requires maintaining context across the separate SSE and POST channels. Session tokens help correlate SSE connections with POST requests, while session timeout and cleanup mechanisms prevent resource leaks. Always store session state securely on the server side to prevent unauthorized access.
To strengthen session management, generate cryptographically secure session identifiers that resist prediction and brute-force attacks. Implement automatic session expiration with configurable timeouts, typically 30-60 minutes of inactivity for standard web applications. Create a background cleanup process that periodically scans for and closes abandoned sessions, running every few minutes to prevent resource exhaustion.
Store session data in a centralized, secure storage system that supports atomic operations to prevent race conditions when sessions are accessed from multiple endpoints. For distributed systems, implement a shared session store using Redis, MongoDB, or similar technologies that maintain consistent state across server instances.
Debugging SSE Transport
The asynchronous nature of SSE transport makes debugging particularly challenging. Enable detailed logging to record all message exchanges with timestamps, which creates a trail you can follow when issues arise. Browser DevTools provide another powerful ally, allowing you to monitor SSE connections in the Network tab.
Additionally, you can also implement heartbeats, which send periodic messages to verify connection health, alerting you quickly when problems occur. Request/response tracing with correlation IDs in all messages helps track the complete flow of communication through your system.
Final Thoughts
SSE transport provides a powerful mechanism for MCP applications that need web compatibility with support for server-initiated messages. While it requires more configuration than STDIO transport, SSE enables MCP to work across network boundaries and with web clients.
As you work with MCP, remember that SSE provides unidirectional server-to-client streaming combined with HTTP POST for client-to-server communication. Security measures play an essential role in implementing SSE transport effectively. Always choose the right transport based on your application's specific requirements and environment.